Entarian are here to help you meet your compliance audit; secure your system by managing every unmanaged account password, and reduce time and risk with an audited controlled access channel to your remote systems.
What we provide
ForestSafe is a fully automated Enterprise Password Management system. There are deployment packages available for any organisation. We support all industry sectors. In the Financial sector we support ATM account management.
Entarian are leaders in Enterprise Systems Management and IT security. We will help you configure Enterprise Password Management in your organisation, and enable you to realise the cost and security benefits of Remote Identity Management.
Why we provide it
- Every unmanaged password; i.e. an accounts with a passwords property set to never to expire, is a risk to your organisation.
- Supplying a fully audited controlled remote SSH Terminal and Remote Desktop access function to your support staff has cost and security benefits
Password Management
There are many account passwords that by default have to be set never to expire. These accounts control the running of Windows services, database server accounts, and accounts embedded in applications.
There are 2 types of accounts, unique password accounts and synchronised password accounts, and these accounts are the most powerful accounts that exist in your system. ForestSafe manages the passwords of any of these accounts.
|
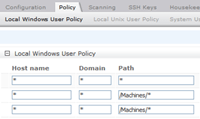
Local Passwords Make every local password in your system unique |
|
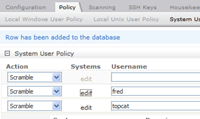
System Passwords
|
|
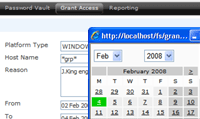
Grant Access
|
Security & Accountability
ForestSafe has several security layers. Some teams may require constant remote access to known lists of servers, others may need occasional access to servers managed by an approver. The system is designed to enable audited control over all system access.
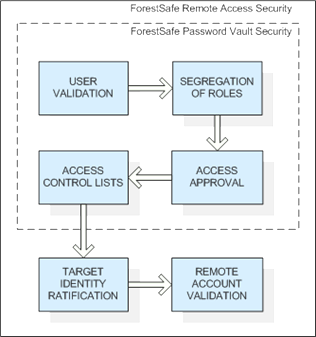
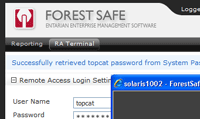
User Validation is the doorway to the remote access.
All ForestSafe users must exist as Windows domain users. Access is via a Web Page either by password entry or Single Sign On.
Segregation of roles is required by ISO27001:2013, COBIT and Sarbanes-Oxley Act. It is vital that partitions exist between the various functions of a system so employees in one section cannot interfere with the work of others.
Every ForestSafe function can be added or removed from the ForestSafe Administrators desktop using Administrator Role Management. Access to system functions is completely granular.
Access Approval is available to apply an extra layer of authority between users and the hosts that are allowed to access remotely.
A ForestSafe approval can to be configured immediately or in the future, and set to terminate at a given time. During this period the Administrator requiring Approval has view of the requested target.
Access Control Lists define which hosts Administrators are allowed to access, and also which user accounts they login with.
ForestSafe is configured to create hierarchies of Access Control Containers (Intelligent access control lists). Administrator Roles are mapped against any container in the hierarchy and will inherit any hosts present in the sub-containers. The ForestSafe Administrator is presented with a restricted list of choices based on either their current approvals, or if approval layer is not enabled, the contents of the host container associated with their Administrator Role.
Target Identity ratification is a final security check, before allowing a remote access, that the host being accessed is the real host and not a Man in Middle attack.
Every ForestSafe host configured for SSH, requests the public SSH key from the host on discovery. This key is stored against the host record and compared every time a remote access takes place.
Remote Account Validation is the final doorway to the remote system.
Validation can be through credential entry or password-free login. If 2 stage login is required (su command on UNIX systems), the Administrator can be given access to the Password Vault to retrieve the su account password.
|
Terminal Access Audited, Identity Managed Terminal Access to your remote systems via single sign-on or retrieved password |

